LazyXSS: A Deep Dive into Automating Reflected XSS Vulnerability Detection
In the ever-evolving landscape of cybersecurity, web application vulnerabilities continue to be a primary concern for organizations and security professionals worldwide. Among these, Cross-Site Scripting (XSS) stands out as a pervasive and potentially devastating threat. Specifically, Reflected XSS, while seemingly straightforward, often evades manual detection due to the sheer volume of parameters and dynamic content in modern web applications. This is precisely where specialized tools become indispensable. Enter LazyXSS: an advanced, Python-based solution meticulously engineered to automate and enhance the precise identification and confirmation of Reflected XSS vulnerabilities.
The Anatomy of Reflected XSS: Why It Matters
To fully appreciate the value of LazyXSS, it’s crucial to understand the mechanics and implications of Reflected XSS. Unlike Stored XSS (where malicious script is permanently saved on the target server) or DOM-based XSS (where the vulnerability lies in client-side code), Reflected XSS occurs when a malicious script originates from the victim’s request and is “reflected” off the web server back to the victim’s browser.
Here’s a typical scenario:
An attacker crafts a URL containing a malicious script as a parameter (e.g., https://example.com/search?query=<script>alert(‘XSS’);</script>).
The attacker then lures a victim into clicking this specially crafted URL, often via phishing emails or malicious links.
When the victim’s browser sends the request to the vulnerable web server, the server, without proper input validation or output encoding, incorporates the malicious script directly into its HTTP response.
The victim’s browser receives this response and, believing the script to be legitimate content from the trusted website, executes it.
The consequences can be severe:
Session Hijacking: Attackers can steal session cookies, gaining unauthorized access to a user’s account.
Defacement: The attacker can alter the content of the web page in the victim’s browser.
Malware Distribution: Victims can be redirected to malicious websites that host malware.
Phishing Attacks: Credential theft can occur if the attacker injects fake login forms.
Data Exfiltration: Sensitive user data displayed on the page can be sent to an attacker-controlled server.
Given these risks, comprehensive and efficient testing for Reflected XSS is not just a best practice; it’s a critical component of any robust web security strategy.
Diving Deeper into LazyXSS’s Core Capabilities
LazyXSS isn’t just another scanner; it’s a meticulously designed tool that addresses common pain points in XSS detection:
Intelligent Automated GET Parameter Scanning: Manual enumeration and testing of GET parameters is incredibly time-consuming and prone to human error, especially in applications with a large attack surface. LazyXSS automates this process entirely. It intelligently parses target URLs, identifies all accessible GET parameters, and systematically injects a variety of carefully crafted XSS payloads into each one. This ensures that no potential injection point is overlooked, providing a truly comprehensive scan. The tool’s ability to identify parameters automatically significantly reduces preparation time for security assessments.
Scalable Multi-Target Assessment from File Input: For penetration testers and security teams managing multiple web assets, the ability to scan numerous targets efficiently is paramount. LazyXSS supports reading target URLs from a file, enabling batch processing. This means you can list dozens or even hundreds of URLs, and LazyXSS will systematically work through each one, applying its automated testing logic. This feature is particularly valuable for large-scale security audits or continuous integration/continuous deployment (CI/CD) pipelines where regular, automated scans of an entire application portfolio are required.
Actionable and User-Friendly HTML Reporting: Raw scan output can often be difficult to parse and act upon. LazyXSS excels by generating comprehensive, well-structured HTML reports. These reports are designed for clarity and ease of use, featuring a clean, modern interface. Each report details:
The specific URL where a potential XSS vulnerability was found.
The exact GET parameter that was vulnerable.
The specific payload that triggered the reflection.
Often, contextual information that helps in quickly verifying the vulnerability. This level of detail streamlines the post-scan analysis, allowing security professionals to quickly identify, prioritize, and articulate findings to developers for remediation.
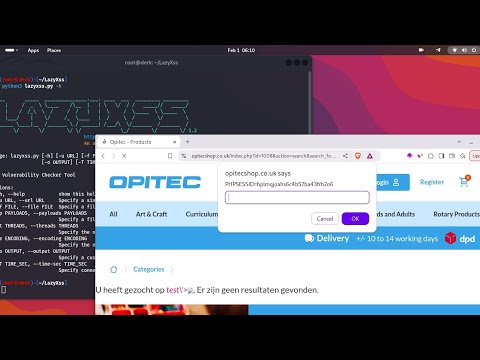
How LazyXSS Detects Reflections: The Technical Underpinnings
At its core, LazyXSS functions by mimicking an attacker’s behavior while leveraging automated analysis. Here’s a simplified technical breakdown:
Payload Generation: The tool employs a diverse set of XSS payloads, ranging from simple <script>alert(1)</script> to more sophisticated vectors designed to bypass basic filters.
Request Construction: For each identified GET parameter in a target URL, LazyXSS constructs a new HTTP GET request, embedding one of its generated payloads into that parameter.
Response Analysis: Upon receiving the web server’s HTTP response, LazyXSS performs a detailed analysis of the HTML content. It looks for the “reflection” of its injected payload. This isn’t just a simple string search; it involves sophisticated pattern matching and sometimes even rudimentary DOM parsing to confirm that the payload was reflected in a way that could lead to script execution in a browser context. This intelligent analysis helps minimize false positives.
Vulnerability Reporting: If a clear reflection is detected that indicates a potential XSS vulnerability, LazyXSS logs the details and includes them in the final HTML report.
This systematic approach ensures high accuracy and coverage, making LazyXSS a reliable ally in uncovering these often-hidden flaws.

Integrating LazyXSS into Your Security Workflow
Incorporating LazyXSS into your existing security testing or development lifecycle can yield significant benefits:
Pre-Deployment Testing: Run LazyXSS as part of your quality assurance (QA) or staging environment testing before new features or applications go live.
Regular Audits: Schedule periodic scans of your web applications to catch new vulnerabilities that might emerge from code updates or configuration changes.
Bug Bounty Programs: For bug bounty hunters, LazyXSS provides a quick and efficient way to scan for common XSS vulnerabilities.
Developer Training: Developers can use LazyXSS as a learning tool to understand how XSS vulnerabilities are exploited and, more importantly, how to prevent them through secure coding practices (e.g., input validation and output encoding).
Ready to Fortify Your Web Applications?
LazyXSS offers a compelling blend of automation, comprehensive scanning, and clear reporting, making it an indispensable tool for anyone serious about web application security. By leveraging this open-source solution, you can proactively identify and mitigate Reflected XSS vulnerabilities, safeguarding your applications and users from potential attacks.
You can access the LazyXSS tool and its complete documentation directly from its GitHub repository:
👉 https://github.com/iamunixtz/LazyXss
Important Ethical Considerations and Disclaimer:
This detailed article and the information contained within are provided strictly for educational and ethical awareness purposes. We unequivocally do not endorse, promote, or encourage any illegal or unauthorized activities. It is paramount that all information and tools discussed, including LazyXSS, be used responsibly, ethically, and in strict compliance with all applicable laws and regulations. When conducting any form of penetration testing or security assessment on web applications, always obtain explicit, written authorization and consent from the asset owner or the relevant parties involved before initiating any scans or tests. Unauthorized testing is illegal and unethical.
Discover the latest developments and news in the world of technology with Trendo.







